Architecture: Blackberry Enterprises Solution
The Blackberry Enterprises Solution has been got used using this component. This is the standard architecture of data flow between the Blackberry devices to Messaging server.

Component Description
BlackBerry device: The BlackBerry device provides Access to email messages, calendar, Contacts, Enterprises Global Address Lookup
Wireless network: The wireless network routes the data to and from the BlackBerry devices to the Internet through the BlackBerry Infrastructure.
BlackBerry Infrastructure: The BlackBerry Infrastructure is designed to provide a highly secure and reliable connection to wireless networks operated by
many service providers around the world.
Internet: The internet component is not mentioned here, however this is very much require to transport the data Internet transports data between the wireless network and the firewall.
Firewall: The BlackBerry Enterprise Server maintains an outbound-initiated, bidirectional connection through port 3101 on the firewall and over the Internet to the BlackBerry Infrastructure.
Introducing the BlackBerry Enterprise Solution
BlackBerry Enterprise Server:
The BlackBerry Enterprise Server is installed on a computer behind the organization’s firewall. The BlackBerry Enterprise Server is designed to
• Manage the wireless transfer of data to and from the BlackBerry devices
• Encrypt all data that flows to and from the BlackBerry devices
• Allow highly secure push delivery of content to the BlackBerry devices
Messaging server:
The BlackBerry Enterprise Server integrates with the following messaging servers to provide wireless delivery of email messages and organizer data
• Microsoft Exchange
• IBM Lotus Domino
• Novell GroupWise
Instant messaging server:
The BlackBerry Enterprise Server integrates with the following types of instant messaging servers to allow highly secure, wireless delivery of instant messages and data:
• Microsoft Office Communications Server
• Microsoft Office Live Communications Server
• IBM Lotus Sametime
• Novell GroupWise Messenger
Application or content servers:
The organization’s application servers or content servers provide push applications and intranet content that the BlackBerry Enterprise Server makes available to the BlackBerry Devices.
Email flow for the BlackBerry Internet Service
This below design we have outlined for the email flow when a blackberry device sends emails to another Blackberry device using Blackberry internet service.
1. An email message is sent from a BlackBerry smartphone. The email message is compressed so that it is in CMIME format and sent to the wireless network.
2. The wireless network delivers the email message to the BlackBerry Infrastructure.
3. The BlackBerry Infrastructure uses the UID field in the [CMIME] service book to deliver the email message to the appropriate BlackBerry Internet Service server.
4. The BlackBerry Internet Service converts the email message to standard MIME format and sends the email message to the Internet. The email message is sent through the Internet using SMTP to the recipient’s messaging server.
5. Then the messages reaches to the recipient users, Then once the recipient replies to that email, the data flow happens as mentioned below.
6. An email message is sent to the BlackBerry smartphone user from an email application on the computer. The email message is delivered through the Internet to the BlackBerry Internet Service.
7. The email message is compressed by the BlackBerry Internet Service so that it is in CMIME format and sent to the BlackBerry Infrastructure.
8. The BlackBerry Infrastructure sends the email message to the wireless network using the current assigned PIN.
9. The email message travels over the wireless network to the BlackBerry smartphone which decompresses the email message.
Email flow for the BlackBerry Professional
The below outline shows – the email data flow in the infrastructure of Blackberry Professional & Messaging server.
1. BlackBerry smartphone User A creates an email message and Sends it. The email message is compressed, encrypted, and sent to the wireless network.
2. The wireless network sends the email message to the Internet through the BlackBerry Infrastructure.
3. The email message reaches the firewall, where it passes through an outbound-initiated, two-way connection to the BlackBerry Professional Software.
4. The BlackBerry Professional Software decrypts the email message, decompresses it, and places it in BlackBerry smartphone User A’s outbox.
5. The messaging server forwards the email message to the recipient in the organization.
6. The BlackBerry Professional Software monitors User B’s mailbox and retrieves the new email message. The new email message is applied against global and personal email message filters. If the email message is being sent to BlackBerry smartphone User B’s BlackBerry smartphone, the BlackBerry Professional Software compresses and encrypts the first 2 KB of the email message and queues it for delivery.
7. The email message is sent by the BlackBerry Professional Software through an outbound-initiated, two-way connection on the firewall to the Internet.
8. The email message is sent through the Internet to the organization’s firewall.
9. The email message arrives at User B’s mailbox.
Email Message flow for the BlackBerry Enterprise Solution
Email messages sent to and from BlackBerry smartphones the following scenario outlines the email message flow when an email message is sent by a BlackBerry smartphone user in one organization
(BlackBerry smartphone User A) and received by a BlackBerry smartphone user in another organization (BlackBerry smartphone User B) through the BlackBerry Enterprise Solution
1. BlackBerry smartphone User A creates an email message and sends it. The email message is compressed, encrypted, and sent to the wireless network.
2. The wireless network sends the email message to the Internet through the BlackBerry Infrastructure.
3. The email message reaches the firewall where it passes through an outbound-initiated, two-way connection to the BlackBerry Enterprise Server.
4. The BlackBerry Enterprise Server decrypts the email message, decompresses it, and places it in BlackBerry smartphone User A’s outbox.
5. The messaging server sends the email message as SMTP traffic through the firewall using the port designated for email messages.
6. The email message travels across the Internet as SMTP traffic and arrives at BlackBerry smartphone User B’s firewall.
7. The firewall allows the email message to pass through to the messaging server, where it is placed in BlackBerry smartphone User B’s mailbox.
8. The BlackBerry Enterprise Server monitors BlackBerry smartphone User B’s mailbox and retrieves the new email message. The new email message is applied against global and personal email message filters. If none of the filters apply to the email message, the BlackBerry Enterprise Server prepares to deliver it to BlackBerry smartphone User B’s BlackBerry smartphone. The BlackBerry Enterprise Server compresses and encrypts the first 2 KB of the email message and queues it for delivery.
9. The BlackBerry Enterprise Server sends the email message through an outbound-initiated, two-way connection on the firewall to the BlackBerry Infrastructure.
10. The BlackBerry Infrastructure sends the email message to the wireless network.
11. The wireless network receives the email message and forwards it to BlackBerry smartphone User B’s BlackBerry smartphone.
12. BlackBerry smartphone User B’s BlackBerry smartphone receives, decrypts, and decompresses the email message. BlackBerry smartphone User B’s BlackBerry smartphone also sends a confirmation notification to the BlackBerry Enterprise Server to indicate that the email message has been received.
Email sent to and from BlackBerry smartphones in the same ORG
The following scenario outlines the email message flow when an email message is created and received by BlackBerry smartphone users (BlackBerry smartphone User A and BlackBerry smartphone User B) in
the same organization through the BlackBerry Enterprise Solution.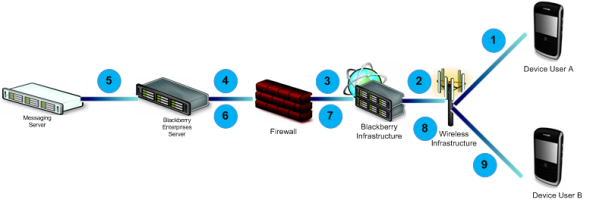
1. BlackBerry smartphone User A creates an email message and sends it. The email message is compressed, encrypted, and sent to the wireless network.
2. The wireless network sends the email message to the Internet through the BlackBerry Infrastructure.
3. The email message reaches the firewall, where it passes through an outbound-initiated, two-way connection to the BlackBerry Enterprise Server.
4. The BlackBerry Enterprise Server decrypts the email message, decompresses it, and places it in BlackBerry smartphone User A’s outbox.
5. The messaging server forwards the email message to the recipient in the organization.
6. The BlackBerry Enterprise Server monitors BlackBerry smartphone User B’s mailbox and retrieves the new email message. The BlackBerry Enterprise Server checks the global and personal email message filters. If none of the filters apply to the email message, the BlackBerry Enterprise Server prepares to deliver it to User B’s BlackBerry smartphone. The BlackBerry Enterprise Server compresses and encrypts the first 2 KB of the email message and queues it for delivery.
7. The BlackBerry Enterprise Server sends the email message through an outbound-initiated, two-way connection on the firewall to the BlackBerry Infrastructure.
8. The BlackBerry Infrastructure sends the email message to the wireless network.
9. The wireless network receives the email message and forwards it to BlackBerry smartphone User B’s BlackBerry smartphone.
10. BlackBerry smartphone User B’s BlackBerry smartphone receives, decrypts, and decompresses the email message. BlackBerry smartphone User B’s BlackBerry smartphone also sends a confirmation notification to the BlackBerry Enterprise Server to indicate that the email message has been received.
Note: To made this Blackberry Flow Design – I had prepard the VISIO Stencils, using that i made it. I will be posting those stencial & the softcopy of the VISIO Diagram, which i have prepared.
28.639644
77.244099








